Welcome to Disclosed.

Each week, 3 readers will win a 1-month PentesterLab Pro license, completely free. Refer a friend to the newsletter to enter.
Shout out to this week’s winners (I will email you):
adityasingh199919
harsh20csu181
badrigoud876
PentesterLab is one of the best hands-on platforms for learning web security, with real-world vulnerabilities, private labs, and practical exercises trusted by professionals and bug bounty hunters worldwide.
Huge thanks to PentesterLab for sponsoring this giveaway and supporting the Disclosed. community. ❤️
By the way, referrals are so low right now that almost everyone who has referred someone has received a PentesterLab license. Your chances of being selected are VERY HIGH

Hey there! This is the last post before DEF CON, which is crazy to say out loud considering how many months of planning and work have gone into Bug Bounty Village. It’s about to all be on full display… I definitely will need a vacation once DEF CON is over.
Related, I’m dealing with some nerve pain so will be rolling around in a rental scooter this year, but if you’re coming to Vegas and see me rolling (literally) please feel free to say hi! Would love to connect with all of you. Don’t forget about the Happy Hour that we’re hosting Thursday night as well. Given that I’ll be at the con all weekend, I will miss a Disclosed drop next week for the first time. Just heads up on that, but I’ll definitely be back.
That said, I was able to collab with shaikhyaser this weekend and pop a couple bugs so maybe we’ll have some money to gamble with while we’re in Vegas 😏
HUGE shout-out to the Critical Thinking podcast for featuring Ariel and I on the podcast this week. If you want to learn more about my story, and the origin of Bug Bounty Village, definitely give that pod a listen.
That’s enough about me, let’s dive in.
P.S. Our BBV green badges are about to sell out and won’t be available for purchase onsite. If you’re coming to DEF CON, this is your last chance to grab one. We have less than 50 units left: shop.bugbountydefcon.com
In This Issue

Community Management in Bug Bounty [🎥 Video]
by Critical Thinking - Bug Bounty Podcast
Harley Kimball (@infinitelogins) and Ariel Garcia (@arl_rose) join the conversation to dive into the world of community management in Bug Bounty. The episode explores how these roles shape the ecosystem, the evolution of Bug Bounty Village at DEFCON, and what’s planned for this year.
Read more →
AI-Driven Exploit for CVE-2025-32433 Demonstrated [🔗 Tweet]
by André Baptista
Check out this tweet discussing an article that details the use of AI to develop an exploit for CVE-2025-32433, showcasing innovative techniques prior to public exploit releases.
Read more →
Bug Bounty Village CTF Prize List is Announced [🔗 CTF]
by Bug Bounty Village
Compete in the Bug Bounty Village CTF at DEFCON for a chance to win in-person prizes like PS5s, Meta Quest 3s, and more, with the prize ceremony on Sunday, Aug 10 at 1 PM in W326. Remote participants can also score rewards including OffSec course vouchers, SecOps gift cards, and Pentesterlab licenses. Register now at bbv.ctf.ae.
Read more →

Have something you want to Spotlight? Tell me.

Pwn2Own Ireland 2025: $1 Million WhatsApp Bounty Announced [🔗 Tweet]
by Trend Zero Day Initiative
The tweet announces Pwn2Own Ireland for 2025, featuring a $1 million bounty for exploiting WhatsApp and introducing new USB attack vectors.
Read more →
GrabSG Celebrates 10 Years with Up to 2X Bounty Multipliers [🔗 Tweet]
by HackerOne
GrabSG is celebrating its 10th anniversary on HackerOne with a campaign featuring up to 2X bounty multipliers and special bonuses starting August 11.
Read more →
AI Pentester XBOW Tops HackerOne Leaderboard [🔗 Tweet]
by XBOW
The tweet announces that XBOW, an autonomous AI pentester, has become the top hacker on HackerOne, with a live demonstration scheduled at Black Hat.
Read more →
HackerOne Expands with New Office in Pune [🔗 Tweet]
by Maharashtra Progress Tracking
HackerOne has announced the opening of a new office in Pune, enhancing its operational capacity.
Read more →
LidoFinance Launches $100K Bonus in Bug Bounty Competition [🔗 Tweet]
by Immunefi
Immunefi announces a new bug bounty competition for LidoFinance, offering a $100,000 bonus pool to incentivize researchers to identify vulnerabilities within the Dual Governance codebase.
Read more →
Swiss Post Launches €230K E-Voting Bug Bounty Challenge [🔗 Tweet]
by YesWeHack ⠵
The Swiss Post's 2025 Public Intrusion Test has commenced, inviting global bug hunters to exploit its e-voting platform for rewards up to €230K, including bonuses for early submissions.
Read more →
Did I miss an important update? Tell me.

Custom Pentesting Report Generator for Burp Suite [🔗 Tweet]
by BApp Store
A newly released Report Generator allows pentesters to produce customized reports directly from Burp Suite findings, with options for PDF and Word formats, significantly streamlining the reporting process.
Read more →
New Caido Update Enhances Workflow Testing Features [🔗 Tweet]
by Caido
The latest update for Caido enhances users' ability to test active and passive workflows during development, improving the debugging process with sample requests and responses.
Read more →
\Have a favorite tool? Tell me.

Exploiting a Logic Flaw in a Coding Platform [🔗 Tweet]
by Nagli
This tweet shares a detailed thread on exploiting a logic flaw in a coding platform, which resulted in unauthorized access to private applications, providing useful insights for fellow researchers.
Read more →
How I find vulnerability can make X(Twitter) lose millions of dollars | by L4zyhacker | Jul, 2025 | Medium [📓 Blog]
by L4zyhacker
The post details the author's journey in discovering a vulnerability in X's payment system concerning the AI service GROK, which could lead to significant financial loss. It discusses technical issues such as rate limits, offers insights into a reward of $1200, and underscores the perseverance required when submitting findings.
Read more →
Mozilla | Report #2995025 - Mozilla VPN Clients: RCE via file write and path traversal [📓 H1 Report]
by Rein Daelman (@reindaelman)
This report details a critical path traversal vulnerability in the Mozilla VPN client that enables remote code execution, emphasizing the importance of sanitizing file paths and showcasing how such vulnerabilities can be exploited.
Read more →
€1500 bounty — How I Bypassed 403 Forbidden and Gained Access to the Intranet Portal. | by Ashar Mahmood | Jul, 2025 | Medium [📓 Blog]
by Ashar Mahmood (@Hx_0p)
The blog post narrates how Ashar Mahmood discovered an Authorization Bypass vulnerability that allowed access to an intranet portal, emphasizing the importance of session management and HTTP request manipulation for effective exploitation.
Read more →
GitHub - sayan011/Immunefi-bug-bounty-writeups-list: curation of all(most) immunefi bug bounty writeups I could find(till now) [📁 Repo]
by sayan011 (@ayan_011)
This GitHub repository offers a curated collection of Immunefi-related bug bounty write-ups, providing valuable insights into past vulnerabilities, research responsibilities, and payout details for new researchers.
View the repo →
Discovering Blind SQLi While Hunting for Geo-Bypass [🔗 Blog]
by Nico Waisman at XBOW
The author shares insights on discovering a blind SQL injection vulnerability during a geo-bypass hunt, including a detailed technical analysis of the methodologies employed.
Read more →
Did I miss an important update? Tell me.

Lessons Learned from Earning $250K with Blind XSS [🎥 Video]
by Ben Sadeghipour (@nahamsec)
This video discusses the author's journey to earning over $250K through Blind XSS and a breakdown of tips and lessons learned throughout that experience.
Read more →
Still not found your first bug? Try IDORs [🎥 Video]
by InsiderPhD
This comprehensive video tutorial explains Insecure Direct Object References (IDOR) vulnerabilities, demonstrating practical exploitation techniques using Burp Suite.
Watch video →
Bug Bounty Tip: Advanced GitHub Dorking for Maximum Results! [🎥 Video]
by Medusa
This video covers advanced GitHub dorking techniques to uncover sensitive data in code repositories, detailing effective search operators and their applications.
Watch video →
Exploring XXE Exploitation in Hex Color Palette Challenge [🔗 Tweet]
by YesWeHack ⠵
The video outlines a Dojo challenge focused on exploiting XXE vulnerabilities and utilizing local DTDs for file exfiltration.
Read more →
Did I miss something? Tell me.

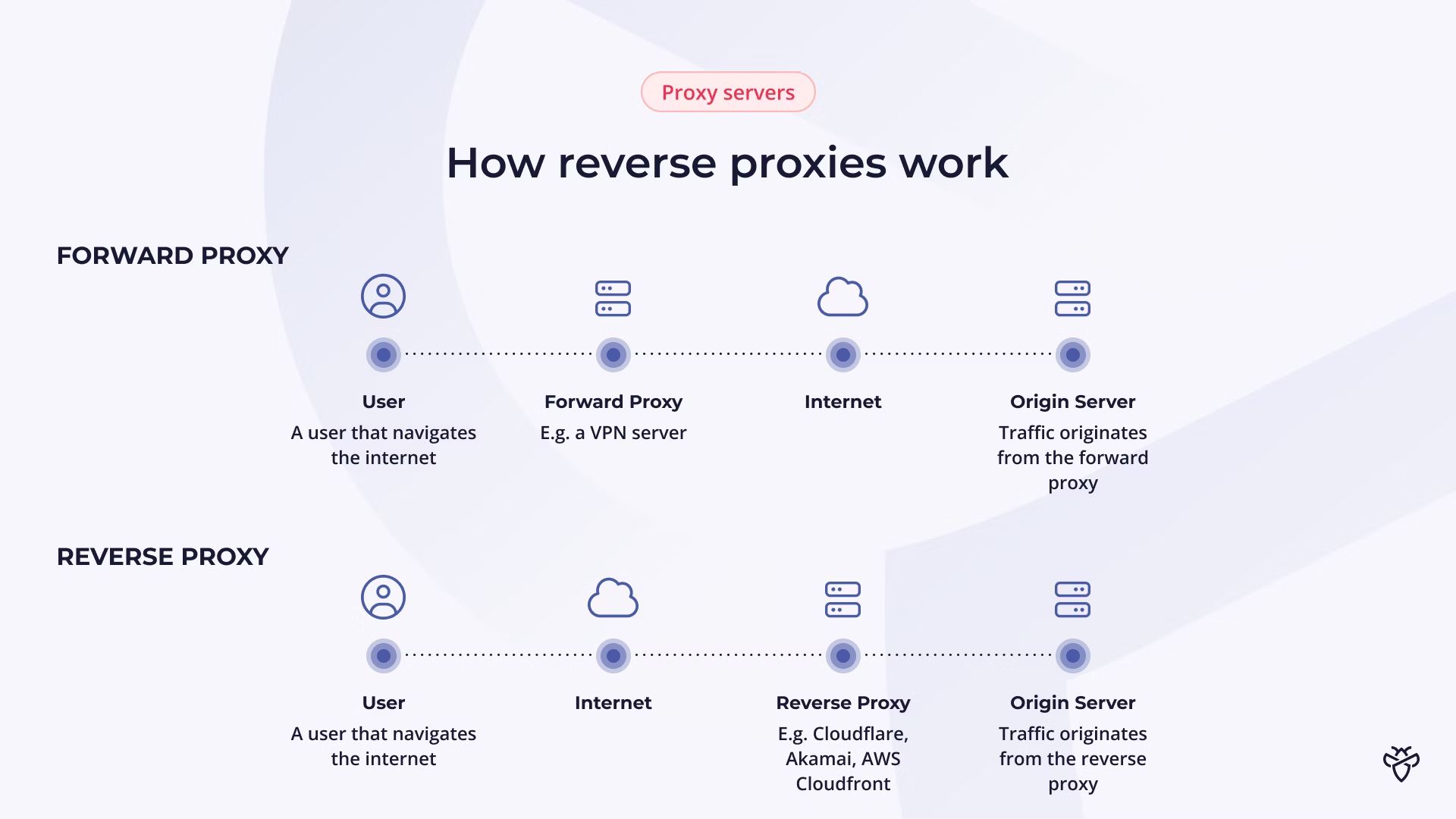
Bypassing Reverse Proxies: How to identify the origin IP [📓 Blog]
by Intigriti
This article discusses techniques for revealing the origin IP of servers behind reverse proxies, crucial for ethical hackers seeking bypass methods for web application firewalls.
Read more →
Secrets of Cross-Site Scripting (XSS [📓 Blog]
by Ahmed Elsayyad
This post dives deeply into Cross-Site Scripting (XSS) vulnerabilities, outlining attack vectors, testing methodologies, and mitigation strategies while providing practical examples.
Read more →

XSS attacks & exploitation: the ultimate guide – YesWeHack [📓 Blog]
by Alex Brumen & YesWeHack
This extensive guide comprehensively covers XSS vulnerabilities, discussing types, detection strategies, and exploitation techniques critical for ethical hackers.
Read more →

Guide to Finding Vulnerabilities Using GitHub Search [📝 Writeup]
by Intigriti
This guide provides practical insights on how to effectively find vulnerabilities through GitHub search, enhanced with relevant examples.
Read more →
Intro to Browser Security Research: Practical Examples and Advice [📓 Blog]
by Ivan Fratrić
This document introduces a guide for browser security research, offering practical examples and addressing the challenges of automation using AI in this space.
Read more →
Prompt Engineering Toolkit for JavaScript Recon (2025 Edition) [📓 Blog]
by Narendar Battula (nArEn)
This guide focuses on the 'Prompt Engineering Toolkit for JavaScript Recon' to improve analysis of common JavaScript vulnerabilities, highlighting the importance of AI in reconstructing actionable intelligence.
Read more →
Did I miss something? Tell me.

Automate Cookie Cleanup in Burp Suite with Regex [🔗 Tweet]
by 🇷🇴 cristi
This tweet shares a regex solution for automatically removing unwanted cookies in Burp Suite, improving the efficiency of the testing process.
Read more →
Live Bug Hunting Breaks Discord Stream Record [🔗 Tweet]
by Critical Thinking - Bug Bounty Podcast
In a recent live-streaming event, numerous bugs were discovered, showcasing the excitement of community participation.
Read more →
Eight Techniques to Obfuscate Transfer-Encoding Header [🔗 Tweet]
by Web Security Academy
This tweet examines eight methods for obfuscating the transfer-encoding header to enhance security testing techniques.
Read more →
Creating Clear Bug Reports for Maximized Bounty Rewards [🔗 Tweet]
by STÖK ✌️
The tweet emphasizes that clear reports and proofs of concept are crucial for successful bounty hunting, helping maximize bounty rewards.
Read more →
Create Your Own VPN Using SSH for Proxying [🔗 Tweet]
by solst/ICE
Learn how to create a VPN-like proxy using SSH tunneling to route browser traffic through a remote host with this tweet.
Read more →
Successful Blind XSS Exploit Leads to $250K Bounty [🔗 Tweet]
by Sleepah
This tweet spotlights a successful blind XSS attack that netted a researcher a $250K bounty, accompanied by a shared example payload.
Read more →
Finding Logic Bugs: Reverse Engineering Steps [🔗 Tweet]
by oussama htb
This tweet outlines a methodical two-step approach for identifying logic bugs in applications through reverse engineering and parameter manipulation.
Read more →
Distinguishing Between ATO and Access Control Bugs [🔗 Tweet]
by bugcrowd
This informative tweet explains the differences between Account Takeover (ATO) bugs and access control issues, enhancing understanding and testing strategies.
Read more →
Essential GitHub Dorks for Vulnerability Discovery [🔗 Tweet]
by Intigriti
This tweet shares a curated list of popular GitHub dorks to facilitate the identification of vulnerabilities in repositories.
Read more →
Did I miss something? Tell me.
Because Disclosure Matters: This newsletter was produced with the assistance of AI. While I strive for accuracy and quality, not all content has been independently vetted or fact-checked. Please allow for a reasonable margin of error. The views expressed are my own and do not reflect those of my employer.
